A large phishing campaign is focusing on organizations using Microsoft Office 365, tricking victims into logging into a spoofed Office online authentication page to steal their credentials and ultimately conduct business email compromise (BEC) scams.
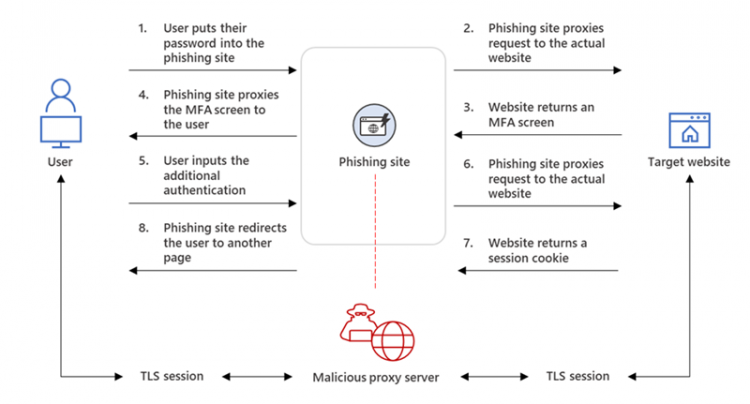
The warning comes from Microsoft, which says the heart of the attack is what it calls adversary-in-the-middle (AiTM) phishing sites. These are impersonated websites that deploy a proxy server between a target user and the website the user wants to visit.
As a result, the attacker can steal and intercept the victim’s password and the session cookie that proves their ongoing and authenticated session with the website, even if the victim has to use multifactor authentication (MFA) to log in.
“Note that this is not a vulnerability in MFA,” says Microsoft. “Since AiTM phishing steals the session cookie, the attacker gets authenticated to a session on the user’s behalf, regardless of the sign-in method the latter uses.”
This attack strategy can be blunted, the report says, by antiphishing solutions and antivirus solutions that detect session cookie theft and attempts to use the stolen cookie to sign into Exchange Online. it can also be defeated by complementing MFA with conditional access policies, where sign-in requests are evaluated using additional identity-driven signals like user or group membership, IP location information, and device status, among others.
Defenders also should continuously monitor for suspicious or anomalous activities, such as sign-in attempts with suspicious characteristics (for example, location, ISP, user agent, use of anonymizer services), and unusual mailbox activities such as the creation of Inbox rules with suspicious purposes, or unusual amounts of mail item access events by untrusted IP addresses or devices.
One common way victims are tricked is they click on a link in a message that purports to be a voice message for them. A fake download progress bar, hardcoded into the HTML file, fools the victim into thinking an audio file is being downloaded. Instead, they are redirected to what appears to be a Microsoft page and asked to log in. The victim’s email address or username, captured during this action, is automatically filled in the form, adding credibility to the scam.
The phishing site could also proxy the organization’s Azure Active Directory (Azure AD) sign-in page, which is typically login.microsoftonline.com. If that had been configured to include the organization’s branding, the phishing site’s landing page also could also copy that, again adding credibility.
When the victim enters their credentials and is authenticated, they are redirected to the legitimate office.com page. However, in the background, the attacker intercepts the credentials, is authenticated first, and gets into the victim’s email.
(How AiTM phishing works. Graphic from Microsoft)
After that, the attacker begins business email compromise (BEC) scams, aided by accessing finance-related emails and file attachments, including ongoing email threads involving payments. Ultimately the attacker tries to trick a target into transferring payments to attacker-owned accounts. One way is by impersonating an employee, replying to ongoing finance-related email threads, and luring the fraud target to send money through fake invoices, Microsoft says.
To protect against detection, the attacker deletes the original phishing email they sent from the compromised account’s Inbox folder. Another defensive tactic by the attacker is to create an email rule along the lines of “For every incoming email where sender address contains [domain name of the fraud target], move the mail to “Archive” folder and mark it as read.”
In one attack, Microsoft says, the threat actor ran multiple fraud attempts simultaneously from the same compromised mailbox.
The report is another example of why ongoing security awareness training is vital in every organization.
While AiTM phishing attempts to circumvent MFA, Microsoft emphasizes that MFA is “an essential pillar in identity security.” Multifactor authentication is still very effective at stopping a wide variety of threats, the report says. In fact, it adds, the effectiveness of MFA is why AiTM phishing has emerged.
Source by www.itworldcanada.com