Facepalm: Anti-cheat software is vital to preserving the integrity of a multiplayer game. However, systems with access to root privileges at the kernel level are dangerous. Security researchers warned of this since this type of cheat mitigation first reared its head, and now it’s being exploited in the wild.
At least one hacker is using anti-cheat software included in the tremendously popular free-to-play MMOPRG Genshin Impact to help mass distribute ransomware. The file is named ‘mhyprot2.sys’ and is described as an anti-cheat driver.
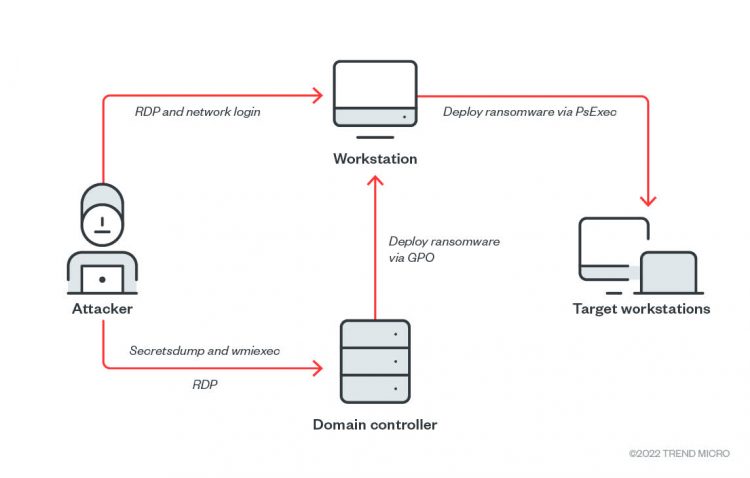
Antivirus vendor Trend Micro received a report in July from a customer who fell victim to ransomware even though his systems had properly configured endpoint protection. When Trend Micro researchers looked into the attack, they discovered a hacker had used a code-signed driver, mhyprot2.sys, to bypass privileges and kill the virus protection with kernel commands.
As of Friday, the code-signing certificate for mhyprot2.sys is still valid. So Windows will recognize it as trustworthy. Furthermore, Genshin Impact doesn’t need to be installed for the driver exploit to work. Malicious actors can use it independently and add mhyprot2.sys to any malware.
The driver has been around since 2020, and a GitHub developer even made a proof-of-concept that demonstrated how someone could abuse mhyprot2.sys to shut down system processes, including antivirus systems. However, Trend Micro said this is the first time it has noticed someone using the driver maliciously in the wild.
“This ransomware was simply the first instance of malicious activity we noted,” reads the report. “The threat actor aimed to deploy ransomware within the victim’s device and then spread the infection. Since mhyprot2.sys can be integrated into any malware, we are continuing investigations to determine the scope of the driver.”
Trend Micro notified Genshin Impact studio miHoYo of the vulnerability, and developers are working on a fix. The problem is that since hackers can deploy the driver independently, any patches will only affect those with the game installed. Plus, hackers will likely pass old versions around their communities for years.
If you’re a business and you run MDE or the like, I recommend blocking this hash, it’s the vulnerable driver.
509628b6d16d2428031311d7bd2add8d5f5160e9ecc0cd909f1e82bbbb3234d6It load straight away on Windows 11 with TPM and all that, the problem has been ignored.
— Cloudflare Support Hate (@GossiTheDog) August 25, 2022
Trend Micro notes it has made specific fixes to its antivirus software to mitigate the driver, but other virus protection suites might miss mhyprot2.sys unless specifically configured to detect it.
“Not all security products are deployed the same and may have certificate checking in different levels of the stack or may not check at all,” Trend Micro’s Jamz Yaneza told PCMag.
It may take a while for other antivirus vendors to catch up. In the meantime, security researcher Kevin Beaumont recommends blocking the diver’s hash (above) if your security suite has hash blocking.
Source by www.techspot.com