The websites of popular business applications from Veeam, SolarWinds, KeePass and PDF Technologies are being spoofed by a threat actor to spread the RomCom remote access trojan (RAT), according to researchers at BlackBerry and Palo Alto Networks.
These reports should be seen as alerts, not only to IT staff, but also to all employees of organizations, of the dangers of downloading applications from websites without approval or without carefully checking the site’s URL.
Not much is known about those behind the RomCom RAT. BlackBerry first wrote about them late last month after they distributed a compromised version of Advanced IP Scanner over the summer, followed by a hacked version of PDF Filer. Then, BlackBerry noted, the group appeared to be targeting Ukrainian military institutions.
In its latest report, BlackBerry says Ukraine still appears to be the primary target, but it also believes some English-speaking countries are being targeted as well, including the United Kingdom.
This report says RomCom is trying to spread remote access trojan-compromised versions of SolarWinds Network Performance Monitor, KeePass Open-Source Password Manager and PDF Reader Pro. Following the release of that report, Palo Alto Networks tweeted that RomCom has also created a fake page for the distribution of a phony version of Veeam Software’s Veeam Availability Suite for Backup.
The threat actor’s campaigns are simple: The creation of virtually identical websites for brand name software providers that organizations might use, by scraping the companies’ original legitimate HTML code. The gang hopes victims will download trial versions or pay for the applications. What they download is infected software.
The BlackBerry report doesn’t say how victims are lured to the sites — whether the threat actor is also sending phishing lures to potential victims or just leaving the fake sites there and hoping they will be discovered.
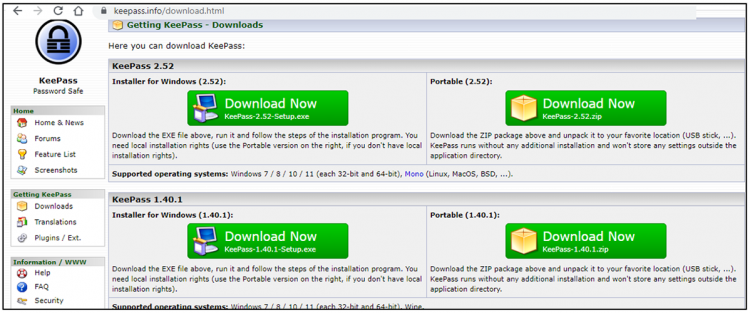
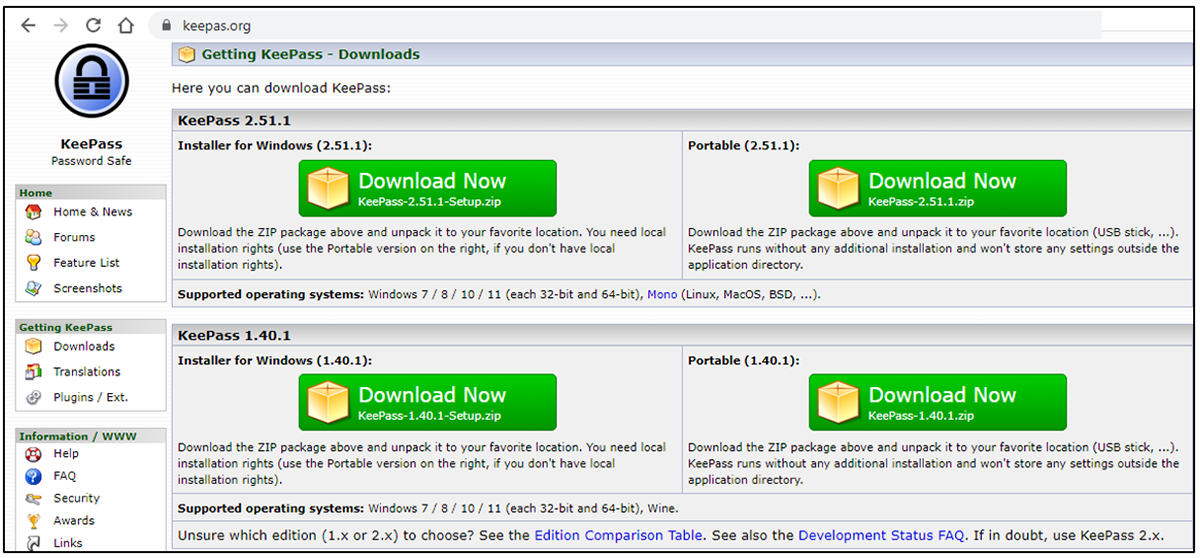
The tip-off, for those with sharp eyes, are the URLs. The phony Veeam website, for example is “wveeam”. The phony KeePass website is “keepas”.
This is a screen shot of a real KeePass site …
… and this is the phony site (images by BlackBerry).
There’s another tip-off, although it would only be found after an application is downloaded: The verification certificate is from a suspicious company. For example, the SolarWinds file contains a digital certificate from “Wechapaisch Consulting & Construction Limited.” The legitimate file is digitally signed by “SolarWinds Worldwide, LLC.”
The scheme goes further. While downloading a free trial from the spoofed SolarWinds site, BlackBerry notes, a legitimate registration form appears. If filled out, real SolarWinds sales personnel might contact the victim to follow up on the product trial. That technique misleads the victim into believing that the recently downloaded and installed application is completely legitimate. Instead, the victim has unknowingly also downloaded a dropper for the malicious remote access trojan.
The BlackBerry report includes indicators of compromise for the RAT.
Source by www.itworldcanada.com