You can never be too careful on the internet, even when you think you are being careful and using proper security systems, those systems could be the problem. At least this is the case with an altered version of the K7Security Suite.
Here is what you need to know about the K7Security Suite and what to be aware of if you are considering security systems for your device.
Malware and the Compromised K7Security Suite
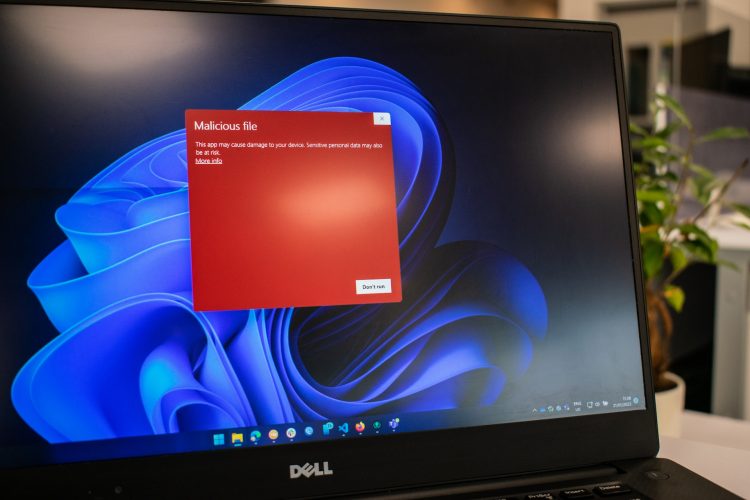
According to various experts, a compromised version of Kaspersky’s famed K7Security Suite is being distributed across the internet. This version looks and acts like Kaspersky’s software, but it actually contains malware in antivirus software setup.
This latest issue was brought to the attention of Kaspersky’s team when employees researched the emergence of Cicada (APT10), which lures people into the false pretense of downloading credible software only for it to be infected by malware itself.
The link that distributed the setup file led users to a page that posed as a genuine Kasperksy software download portal. The file kept the guise going even through the setup process, where it installed the K7Security Suite as the user intended. But it was only after installation that users found the destination folder to be infected by LODEINFO.
What does the Malware Do To Your Device?
This malware not only kills processes and shares your file lists, but also executes shellcode and PE files. It doesn’t stop there, and goes on to upload private files and download malicious files.
The malware in antivirus software is so well-hidden that it duped many professionals in Japan to download it while thinking that they were installing the genuine Kaspersky K7Security Suite. But it was only after Kaspersky’s identification that the problem was brought to the surface.
Be Aware of Potential Threats As You Browse Around on The Web
It has not been found how many people or businesses were affected by this latest dirty trick by bad actors. However, it is easy to assume that the uploading of files points towards stealing private information. Since many of the Japanese employees who were affected by this malware worked at government agencies, targeted espionage also remains in play.
While this investigation goes on, make sure that you are checking the address bar of your browser when downloading any antivirus software. If the page doesn’t come from your antivirus publisher’s main domain, steer clear from downloading anything that it offers to you. This little safety tip can save you from a world of pain.
SUBSCRIBE TO OUR NEWSLETTER
Join our newsletter for tech tips, reviews, and exclusive deals!
ONE MORE STEP IS NEEDED!
Please confirm your email address in the email that we just sent you.
Source by geekinsider.com